What is A Risk Assessment Matrix?
Learn how to apply a risk assessment matrix in this article.
Introduction
When discussing data security, risk is a crucial aspect. This often involves governance, risk, and compliance. With risk management being a key part of your security efforts. Risk assessments can be conducted across various areas and contexts. A risk assessment is based on a specific model and method. Depending on the content applied, it can be used for different purposes, such as GDPR, NIS2, ESG, CSR, anti-money laundering, and more.
Discover what governance, risk, and compliance entail.
This article focuses on risk assessments within the realm of data security. This might include assessing risks related to personal data and GDPR. Or risks associated with cyber-attacks and what we refer to as ISMS, meaning information security management. The method for conducting a risk assessment and using a risk assessment matrix is universal. And you can apply the approach from this article more broadly than the examples mentioned.
The article introduces you to risk assessments and risk matrices. How to work with these tools. And finally, an example of how to conduct a risk assessment using the method.
What does risk assessment mean?
A risk assessment is your chance to proactively manage potential risks to your business. This can help prevent data breaches. Which could damage your company's reputation, hinder product sales, and lead to fines.
Thus, risk assessments become an essential part of your compliance efforts. It's crucial to consider risks across various areas. For instance, if you process personal data of employees and/or customers, you need to perform a risk assessment on this data. Focusing on potential risks to the individuals you're responsible for. Most organisations also assess risks associated with their IT systems. Focusing on the business risks that arise with the adoption of more IT systems. Finally, a cyber-risk assessment may also be relevant. Especially with the introduction of the NIS2 directive. This requires many companies and organizations to identify critical business units and assess the risk of cyber threats to these.
Risk assessment covers a wide range. But the common denominator is identifying relevant risk scenarios depending on the context. Then, you evaluate at a process or system level the consequences if this scenario becomes reality, and its likelihood. With these two assessments, you can make a risk evaluation. This is done through your risk matrix, which this article will delve into further.
What is the difference between InfoSec and Cyber Security?
What are the steps of risk assessment?
Performing a risk assessment involves a series of tasks. In this article we divide them into five overarching steps.
Identify risks
First and foremost, you need to identify the risks you are dealing with. It’s crucial that you keep both the context and area in mind. You can beneficially identify a series of overarching risk scenarios, which you can actively use in your risk assessments. Looking at decisions and data breaches within your area of interest can be helpful. You can find an overview from the local supervisory authorities. In Denmark for example, from the Danish Data Protection Agency.
If you’re conducting a risk assessment on GDPR, a risk scenario could be “do you store data in ceased systems?” and for NIS2 it might be “what is the risk of unauthorised access to the device via phishing attacks”.
You can define your own risk scenarios, choose at what level you define them and how many. Or you can get help with this, for example, via a platform like Privacy. (Read more about the risk module in Privacy here).
Analysis
Next, you move on to the assessments themselves. Decide whether you have a system-driven or process-driven approach to your risk assessments. If you opt for a process angle, you must conduct the risk assessment on all your mapped processes. For each scenario, you assess consequence and likelihood. Remember to justify why you have chosen those particular assessments.
The same applies to the system angle, where you map your systems. Go through your defined scenarios and analyse them from that perspective.
You might also want to read: How to make a data mapping with our simpel Data mapping tool
Evaluation
With your risk assessments in hand, you can categorise them as “red”, “yellow”, and “green”. Here, as an organisation, you have identified your risk appetite, where some organisations accept a yellow risk and others do not. As a rule, you should always act on a red, that is, high or very high risk.
When evaluating risk, you need to identify where the risk has arisen. Then, you should plan how you can reduce this risk.
How can you make a risk assessment? Read our article about that subject and get a framework + example on the topic.
Risk mitigation
The most common method for reducing your risk is to implement mitigating measures. Here, you can focus on the consequence and how to reduce it. When dealing with personal data, the consequence often depends on how much and what kind of personal data you process about the individual. Therefore, one way to reduce the consequence for the individual is to minimise data in the process or system.
But you can also work to reduce the risk by decreasing the likelihood of the scenario becoming reality. Here, you could implement enhanced security measures. These can be both technical and organisational in nature.
Examples include: Consider implementing encryption for data security and regular training for employees on phishing awareness as a combination of technical and organisational measures.
Subsequently, you must document your mitigating measures and update your risk assessments accordingly. The result should ideally be that the risk has been reduced.
Monitoring & review
As with much other compliance work, it is important that you continuously update and review your risk assessments. Therefore, it’s advantageous to plan an activity in your compliance task management that regularly reminds you and your colleagues to go through your risk assessments and see if updates are needed.
By continuously reviewing your risks, you can also be aware of new risks that arise and thus always be proactive and act on them.
What is a risk assessment matrix?
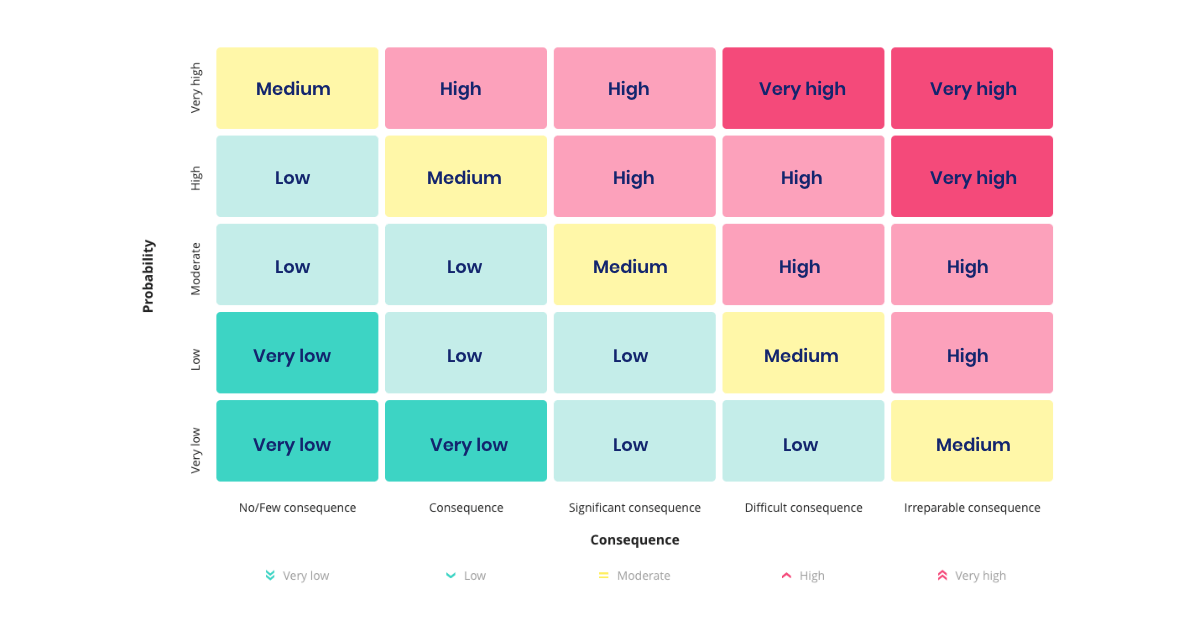
A risk assessment matrix is a tool that you can use to identify a risk score based on your assessment of likelihood and consequence. The matrix is a coordinate system with one axis for consequences and one for likelihood. Typically, you'll see a 5x5 matrix, but some organisations opt for a 4x4 or 3x3 matrix. The key is to choose the size of your matrix based on the scores you assign to consequence and likelihood. So if you assess both consequence and likelihood from 1-5, then you should also use a 5x5 risk matrix.
Scores can often be categorised with names, ranging from "Very low" to "Very high".
The risk assessment matrix serves several purposes. It's both a tool you can use to calculate your risk and can also serve as a reporting tool. It's easy for you, your colleagues, and management to gain an overview of the risks when they are presented visually. Therefore, you can advantageously base your compliance reporting on your risk matrix.
Why is a risk matrix important?
A risk assessment matrix is crucial for a business's security and efficiency for several reasons:
-
Compliance: A risk assessment matrix helps ensure your business complies with relevant regulatory requirements, such as GDPR and NIS2. By identifying and assessing risks, you can take necessary actions to remain compliant. And reducing the risk of sanctions and fines.
-
Risk Overview: Offering a clear and structured visual overview of potential risks. A risk assessment matrix aids leaders and decision-makers in understanding the risk landscape. This overview enables prioritising risks and more effectively allocating resources.
-
Proactivity: Early identification and management of risks are key to avoiding serious repercussions. A risk assessment matrix allows the business to act proactively. By spotting threats before they evolve into actual problems, saving time and resources.
-
Decision-making Support: The risk assessment matrix serves as a valuable tool for management. By supporting informed decision-making processes. It enables assessing risks against business objectives and making well-considered decisions on risk management.
-
Risk Awareness: Promotes a culture of risk awareness throughout the organisation. As employees, management, and the board become accustomed to regularly using and discussing the risk matrix. An understanding and managing of risk can become an integral part of daily operations.
-
Communication Tool: A risk assessment matrix offers a clear and understandable format for communicating about risks. It facilitates illustrating and conveying complex risks to management. And ensuring all stakeholders have a common understanding of the risks and the necessity to act on them.
-
Ongoing Monitoring: Allows for continuous assessment and updating of the company's risk status. This ensures that the business can quickly and efficiently adapt to changes in the risk landscape. And maintain resilience against threats.
Therefore, the risk matrix is an indispensable tool in any business's risk management strategy. It ensures potential threats are identified, understood, and managed effectively, supporting a secure and sustainable operation.
How to create a risk matrix template in 3-4 easy steps?
Creating a risk matrix involves a few clear steps:
-
Choose the number of levels: Determine how many levels you will assess your risk on - 3, 4, 5, or perhaps 6? Based on this, draw your risk matrix with these levels on each axis.
-
Risk division in the matrix: Consider how you will divide your risk within the matrix. When is a risk considered low, medium, and high? The choice of levels is up to you, but it is crucial that you can justify your division. For instance, if the majority of your risk matrix indicates low risk, you should be able to explain why. Using colours to denote different risk levels in your matrix can be beneficial.
-
Utilise your risk matrix: The risk matrix serves both as an overview and an active tool for determining the risk score for a specific scenario. For example, imagine assessing the risk of storing personal data in phased-out systems. You judge the consequence to be 2, as potentially there could be personal data in these systems, but the nature of the data is not critical, as it concerns contact information. The likelihood is assessed at 3, because you have a phased-out IT system not fully decommissioned, and no anonymisation measures are implemented. To determine the risk for this specific scenario, you first locate the field by moving 2 steps on the consequence axis and 3 steps on the likelihood axis. This places you in a field under "low" risk, indicating your risk score for the scenario.
Read about: GDPR Compliance to be aware of when using Cloud Services
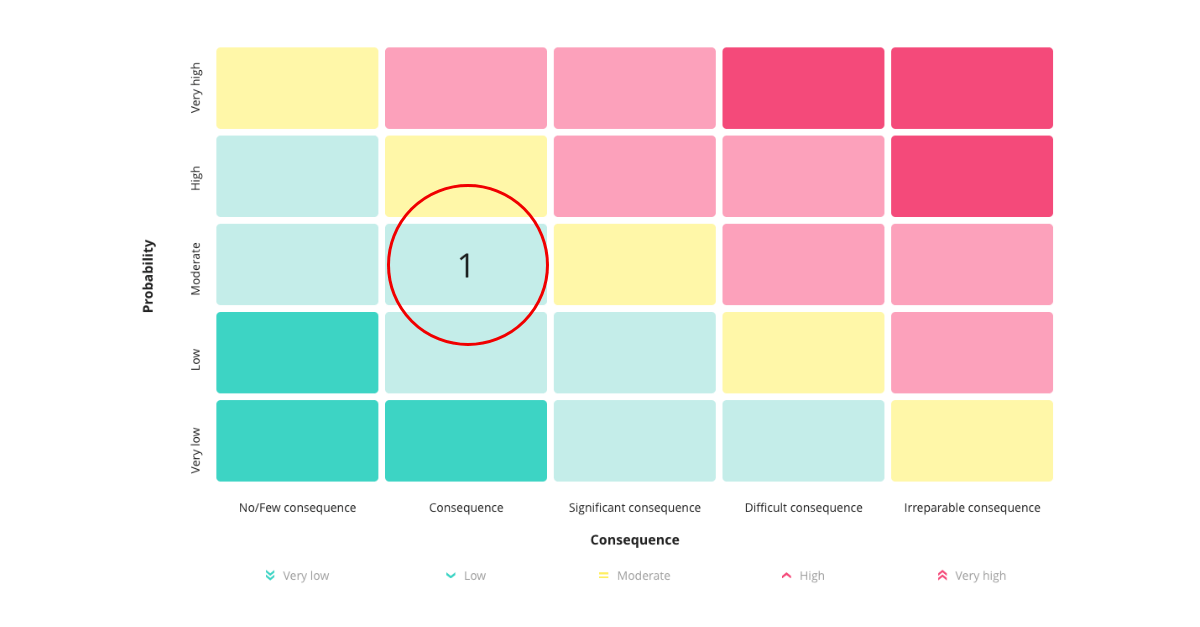
-
Calculate your risk: Alternatively, you can opt for an approach where you calculate your risk based on a score. Instead of letting the matrix fields determine the score, you can use a simple formula: Consequence * Likelihood = Risk. You need to define your risk levels again, for example:
-
Very low risk = 1-2
-
Low risk = 3-6
-
Medium risk = 7-9
-
High risk = 10-15
-
Very high risk = 16-25
-
By using this calculation as a basis, you can also set up an Excel sheet that, based on your assessments of consequence and likelihood, provides an overview of the risk score for your processes, activities, or systems.
You might also be interested in: What is the difference between Excel and Compliance software?
What is the goal of risk assessments?
The primary aim of conducting risk assessments within an organisation is to minimise potential negative impacts. This is achieved through several specific goals:
-
Ensure Compliance: One of the main objectives is to ensure that the organisation complies with relevant legal requirements. Such as GDPR and NIS2. By identifying risks associated with non-compliance, the organisation can take proactive steps to avoid fines and other sanctions.
-
Prevent Negative Consequences: By identifying and proactively managing risks, the organisation works to prevent incidents that could harm the company's finances, reputation, or operations. This includes everything from data breaches to system failures.
-
Support Informed Decision-making Processes: Risk assessments provide management with a clear overview of potential risks. Enabling well-informed decisions on where resources and efforts should be allocated to minimise risk.
-
Promote Risk Awareness: Integrating risk assessments into the organisation's daily operations increases awareness and understanding of risks at all levels within the organisation. This creates a culture where risk management becomes an integral part of all decision-making processes.
-
Achieve Continuous Improvement: Risk assessments are not a one-time event but an ongoing process. By regularly re-evaluating and adjusting risk assessments, the organisation ensures that it can adapt to new threats and changes in the external environment, leading to continuous improvement in security and risk management practices.
Through these goals, organisations strive to create a safe, stable, and sustainable working environment where potential threats are identified, understood, and effectively managed before they can cause harm.
How can .legal help with risk assessment?
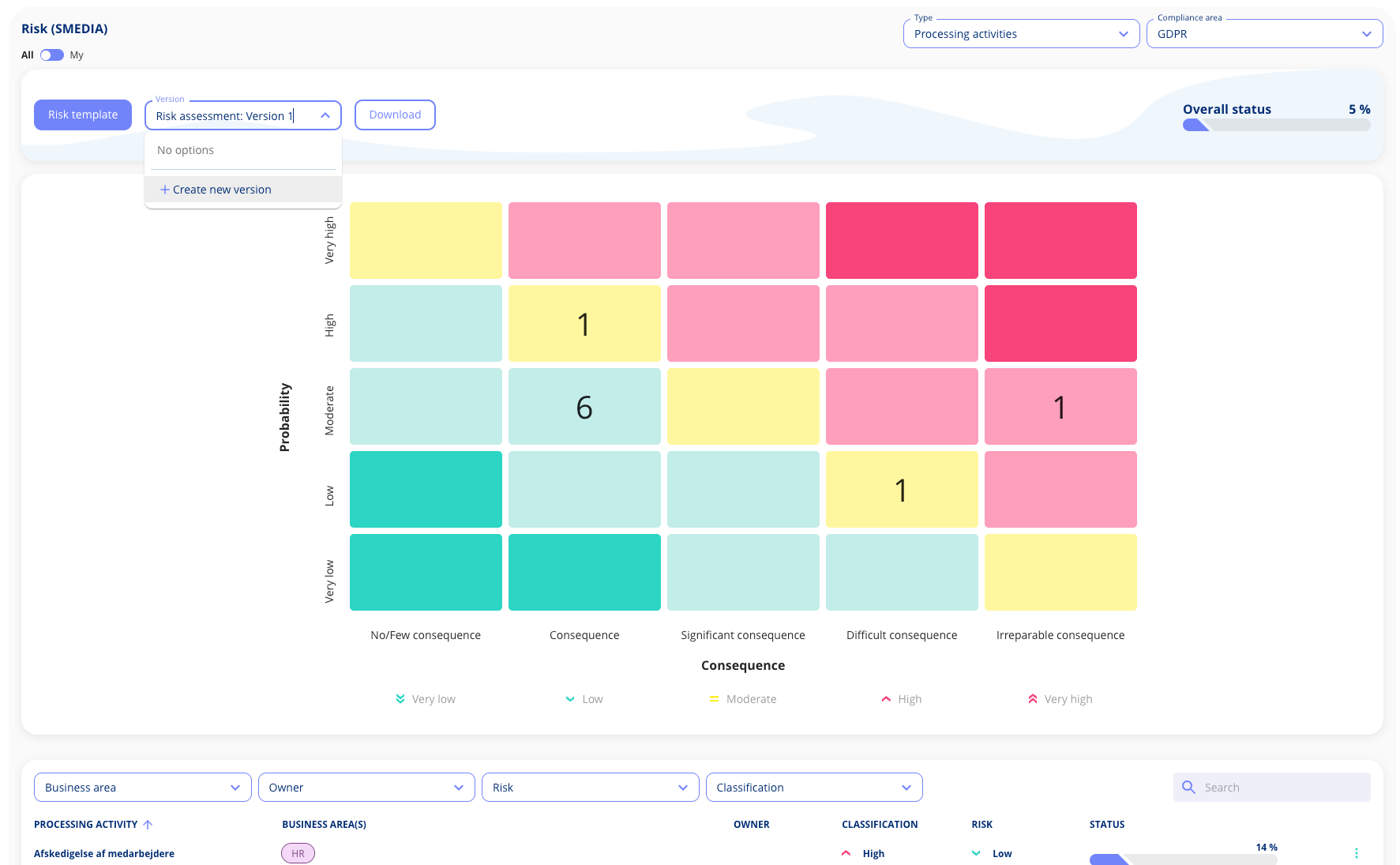
Facing the challenge of conducting risk assessments but unsure where to start? Then .legal's compliance platform, Privacy, might be the solution for you. You can use the platform for free.
We've developed Privacy as a GRC platform, where risk assessments naturally play a central role. Here, you gain access to our intelligent risk module. Offering you a framework tool, a calculation engine, and examples of risk scenarios and threat landscapes. Specifically for GDPR and NIS2.
Read more about our GRC software here.
You can perform risk assessments on both your work processes and systems. Allowing you to choose the most relevant approach for your business. Privacy provides a risk matrix so you can always generate a visual report of your risk assessments. Serving as an effective communication tool with management.
One of the major advantages of using a compliance platform like Privacy is that it facilitates easier collaboration on tasks between you and your colleagues. This way, the responsibility of conducting risk assessments can be distributed more broadly across the business. Allowing multiple employees to contribute while still achieving a unified overview.
So, if you're looking for a structured framework, an efficient tool, and a helping hand to get started with your risk assessments, Privacy might be right for you. The platform and its risk module can be used entirely for free, and you can get started in just two minutes.
By the way: An important part of your risk assessment is that you also assess the risks of your suppliers and not just yourself. In other words, it's important to consider the entire value chain. In addition, it's a good idea to monitor your suppliers on an ongoing basis. Read our articles on the subject here.
How to conduct smart data audits.
GDPR Compliance Software




.jpeg)

.jpg)
.jpg)



.jpg)

-1.png)



.jpeg)








.jpg)





Info
.legal A/S
hello@dotlegal.com
+45 7027 0127
VAT-no: DK40888888
Support
support@dotlegal.com
+45 7027 0127
Need help?
Let me help you get started

+45 7027 0127 and I'll get you started
.legal is not a law firm and is therefore not under the supervision of the Bar Council.