- Product
- .legal platform
- Information Security

INFORMATION AND CYBERSECURITY Comply with information and cybersecurity standards
Meet the requirements of the NIS2 Directive and follow ISO 27000 standards effortlessly. Our module makes compliance processes more efficient through automation, saves time, and enables your entire team to collaborate seamlessly.
-
Centralise all your information and cybersecurity management in one place.
-
Access our framework templates: ISO/IEC 27001:2022, NIS2 - General Requirements and NIS2 – Energy.
-
Conduct risk assessments of your systems and processing activities based on NIS2 risk scenarios.
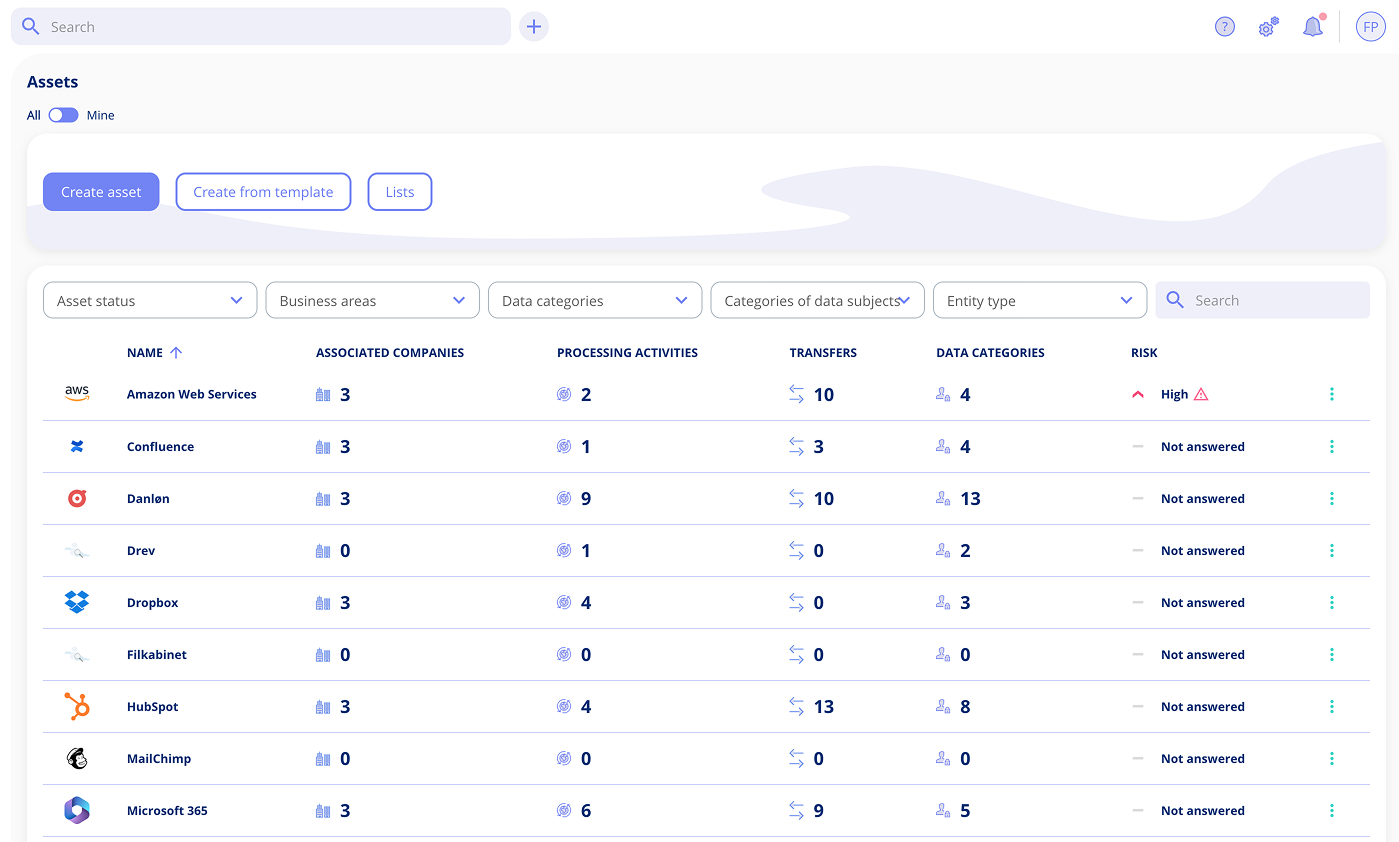
FEATURES Complete control over information security
-
Create a unified overview of the organisation's assets and systems.
-
Create systems based on templates.
-
Register relevant information about connections, data storage, suppliers and much more.
Feature highlights
-
Smart asset management
Register and organise all assets whether they are hardware, software, cloud services or other resources.
-
Template library
Save time with system templates for popular systems with predefined information about the supplier, etc.
-
360-degree system view
See all relationships between systems, suppliers, processing activities and responsible parties in one place.
-
Incident log
Maintain and track all security incidents with automatic versioning.

FEATURES Framework templates for NIS2 and ISO 27001
-
Comply with NIS2 and ISO 27001 using our framework templates.
-
Follow a structured approach to compliance with predefined tasks.
-
Save time with automatic mapping between different frameworks.
Feature highlights
-
NIS2 framework
Meet all minimum requirements for risk management, incident handling and reporting. Ensures correct registration and organisational security.
-
ISO/IEC 27001:2022 framework
Establish requirements for implementation, maintenance and continuous improvement of your ISMS with focus on confidentiality, integrity and availability.
-
Task management and responsibility
Assign tasks to team members with deadlines and automatic reminders.
-
Custom frameworks: ISAE, SOC, CIS18
Create your own compliance frameworks such as ISAE, SOC2 and CIS18 and customise them to your specific needs.
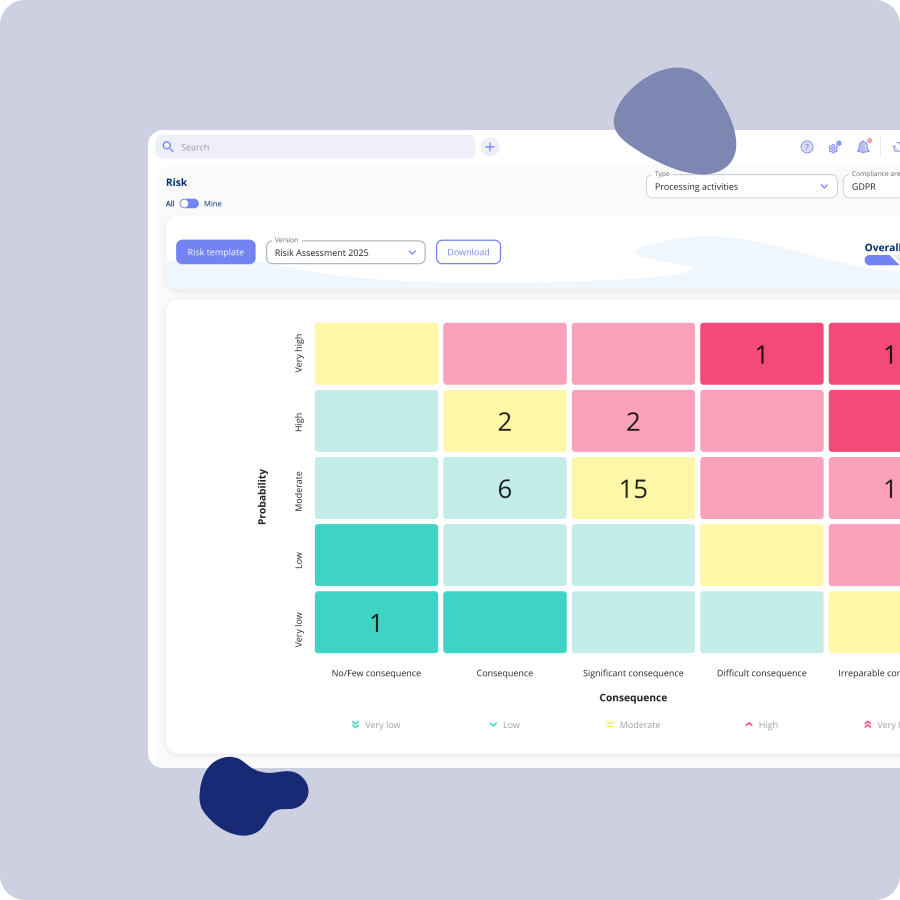
FEATURES Effective risk assessment: Security and compliance from all angles
-
Conduct risk assessments for IT security and NIS2.
-
Choose a system-based or process-based approach to your risk assessments.
-
Access our predefined threat scenarios for IT security and NIS2.
Feature highlights
-
Threat catalogue
Access a catalogue of risk scenarios within IT security and NIS2.
-
Risk matrix
Get an overview of how your risks are distributed in a matrix.
-
Risk assessment
Create individual risk assessments for all systems or processing activities in which the system is involved.
-
Incident log and risk management
Maintain a detailed incident log and manage risks effectively with our module.
Our Customers
-
+400
companies
-
+10.000
users
-
+79.000
contracts
-
+14.000
processing activities
-
Lægeforeningen Michael Berner (Lawyer).legal has been the right choice for us. .legal are professional and welcoming with skilled employees.
-
Min By Media Tinna Schultz (HR manager)It just works! It is so easy and user-friendly, and the overview of processing activities is brilliant.
-
Bech-Bruun Mikkel Friis Rossa (Partner).legal's team has consistently demonstrated a commitment to innovation while being responsive to the needs of our mutual clients.
-
DMJX Kaspar Rochholz (GDPR coordinator).legal has really understood what it means to create a user-friendly and efficient solution. Privacy is an attractive product compared to price and functionality.
-
Axel Kaufmann ApS Julie Lundkvist Andreasen (Lawyer and Head of Customer Service).legal continuously update the platform to ensure their customers always remain compliant. In our view, any other choice would be a downgrade.
-
Molecule Consultancy Nanna Rodian Christensen (HR & Operational Manager)Firstly, it means that not all the work is in one place (me), and secondly, that the understanding of GDPR is implemented throughout the organisation.
-
Fenerum Rasmus Boutrup (Financial Controller)With .legal, we've gained a simpler and more manageable solution that better suits our needs
-
Novicell Julie Oxenvad (Legal Consultant)We are satisfied with the switch to .legal – it has strengthened our compliance work, made processes easier to manage and more transparent, and improved cross-team collaboration

Getting You Started Customer Support
-
You get a dedicated Customer Success Manager.
-
Personal onboarding to ensure a smooth start.
-
Support available Monday to Friday, 9 AM to 3 PM.
Sign up for Information Security today
Get started for free and upgrade to a paid plan when and if you want.
No commitment - Unlimited time on free plan - No credit card needed
Information Security
EUR 135
pr. month
-
All InfoSec standard features
-
Unlimited users
-
Onboarding and support
Monthly payments, no commitment.
Add-ons
Enhance your compliance platform with add-ons.
-
Audit declarations
Controls and documentation required for audit declarations such as ISAE 3402.Read more about Declarations -
User and role management
Keep track of the functions and data that each user has access to.Read more about roles -
Custom lists
Create dynamic lists and reports with automatic updates.Read more about lists -
Single Sign-On
Give your employees secure access with their existing login.Read more about SSO -
GDPR in research projects
For easier interaction between researcher and case officer.Read more about GDPR in Research -
Group companies
Differentiate between the individual companies' compliance.Read more about Group compliance -
Contract obligations
Create better overview with obligations in your contracts.Read more about contract obligations
.legal's Compliance
-
ISAE 3402
ISAE 3402 certificat -
ISAE 3000
Download a copy of .legal A/S’s latest ISAE 3000 (Type 2) report on our GDPR compliance.ISAE 3000 certificat -
Data Processing A (DPA)
Data Processing AgreementFind .legal A/S’s data processing agreement here.
-
IT Security Measures
.legal's Security MeasuresAll of .legal A/S’s implemented and approved IT security measures are described here.
Frequently asked questions about information and cyber security software
What is information and cyber security software?
A system that helps organisations manage and document their information and cyber security. The software supports compliance with NIS2 and ISO 27001 through asset management, risk assessment and automated documentation.
Learn more about the difference between information and cyber security
How does .legal help with NIS2 compliance?
.legal offers a complete NIS2 framework with predefined tasks covering requirements for risk management, incident handling and reporting. Includes risk assessment based on NIS2 scenarios and automatic documentation.
Read the introduction to NIS2
Can I use the platform for ISO 27001 certification?
Yes, .legal includes the ISO/IEC 27001:2022 framework with all necessary controls and documentation requirements. The platform supports implementation, maintenance and continuous improvement of your ISMS.
Learn about ISO 27001 compliance
What does automatic mapping between frameworks mean?
When you complete information in one framework (e.g. NIS2), relevant parts of other frameworks (e.g. ISO 27001) are automatically updated. This saves time and ensures consistency without duplicate work.
See all frameworks
How does risk assessment work in the platform?
The platform offers system and process-based risk assessment with predefined threat scenarios. You can assess risks, visualise them in a risk matrix and link security measures directly to identified risks.
Learn about information security risk management
What is a threat catalogue?
A library of predefined risk scenarios for IT security and NIS2. It contains typical threats such as cyber attacks, data exfiltration and system failures, making it easier to identify relevant risks.
Can I customise frameworks to my organisation's needs?
Yes, in addition to NIS2 and ISO 27001, you can create custom frameworks such as ISAE, SOC2 and CIS18. Customise controls, tasks and requirements to your organisation's specific needs.
Learn about ISAE 3402
How are security incidents handled in the platform?
The platform has an incident log where all security incidents are registered with automatic versioning. Incidents can be linked to systems, risks and corrective measures.
What are system templates?
Predefined templates for popular systems that automatically populate information about vendors, data processing and security measures. This saves time and ensures consistent documentation.
Read introduction to ISMS
How do I get started with the platform?
Start on the free plan with no credit card required and no commitment. You get personal onboarding, a dedicated Customer Success contact and support on weekdays 9am-3pm.
Book a demo



.jpeg)

.jpg)
.jpg)



.jpg)

-1.png)



.jpeg)








.jpg)





Info
.legal A/S
hello@dotlegal.com
+45 7027 0127
VAT-no: DK40888888
Support
support@dotlegal.com
+45 7027 0127
Need help?
Let me help you get started

+45 7027 0127 and I'll get you started
.legal is not a law firm and is therefore not under the supervision of the Bar Council.