GDPR Risk Assessment: Complete Guide with Practical Examples
Master GDPR risk assessment with proven frameworks, step-by-step guidance, and real-world examples to protect personal data and ensure compliance.
TL;DR – Key takeaways on GDPR Risk Assessment
-
Take a risk-based approach to prevent data protection issues.
GDPR risk assessment isn't just about documentation – it identifies where personal data could be at risk and prevents incidents before they happen. -
Use structured frameworks for consistent GDRP risk assessments.
A clear framework helps you map processing activities, create realistic threat scenarios, and assess risks based on likelihood and impact. -
Leverage DPIAs and risk matrices for better decisions.
Data Protection Impact Assessments and visual tools like risk matrices support informed decisions and help justify your approach. -
Keep risk documentation current and relevant.
Risks evolve over time. Regular reviews ensure assessments reflect current practices, systems, and legal requirements. -
Simplify GDPR risk assessments with the right compliance platform.
A GDPR compliance platform like .legal gives you predefined scenarios, built-in guidance, and automation – saving time and reducing complexity.
Introduction
The General Data Protection Regulation (GDPR) is fundamental to data protection for businesses in the EU. You might have already taken significant steps in your GDPR journey.
Perhaps you've compiled your Record of Processing Activities, updated your privacy policy on your website, and have full control over your cookies. Maybe you have an annual plan to keep your documentation up to date.
Yet, GDPR risk assessment remains challenging for many. Carrying out risk assessments on your data processing activities can seem overwhelming. This often stems from lacking an effective framework to guide the process. A risk-based approach to GDPR is extremely important – it enables you to act proactively in your work with personal data.
Much like other GDPR tasks, a solid framework makes GDPR risk assessments more manageable. In this article, we explore the critical elements of effective risk assessment, why it matters, and offer suggestions for designing your framework. You'll also find a concrete example of what a GDPR risk assessment could look like.
Read also: What does Governance, Risk and Compliance mean?
Essential GDPR Risk Assessment Components
Managing data privacy risks builds trust with stakeholders while meeting legal obligations. Below are key components of an effective GDPR risk assessment process:
Proactive Threat Identification
Begin by actively identifying and assessing potential threats to your data. A comprehensive framework guides you through various aspects of the risk assessment process. Map processing activities involving personal data first. This sets the stage for creating risk scenarios to visualise potential threats. The proactive nature prevents incidents before they occur.
Strengthening Data Privacy Programmes
Strengthening your data privacy enhances your overall privacy programmes. It's not just about ticking compliance boxes – it's about creating a culture where data protection is integral to all operations. The objective is making well-informed decisions without falling into 'analysis paralysis.' A structured framework enables you to integrate data protection measures effectively.
Data Protection Impact Assessments (DPIAs)
Data Protection Impact Assessments (DPIAs) are essential tools for measuring privacy programme effectiveness. They add scrutiny, helping you understand real risks involved in each data processing activity. Using detailed information from specific processing activities, DPIAs enable comprehensive understanding of risks and appropriate action.
Data Minimisation and Retention Policies
Data minimisation and crafting precise data retention policies are fundamental practices for reducing risks. Limit data collection to only what's necessary for the designated purpose, and establish clear guidelines on retention periods. These practices minimise the surface area for potential threats and help align with GDPR's data minimisation principle.
Monitoring Privacy Programme Deadlines
Stay ahead by continuously monitoring your privacy programme's deadlines and industry trends. Whether it's compliance audits or updating policies, track when and what needs doing. Paying attention to the evolving privacy landscape allows you to adapt strategies effectively.
Effective risk management is the foundation of resilient data privacy programmes. A balanced approach blending legal compliance with proactive privacy culture proves most effective.
Understanding GDPR Risk Assessment
A GDPR risk assessment reviews the personal data an organisation processes to identify and evaluate associated risks. GDPR's main aim is ensuring protected handling of personal data. This means being clear about what personal data you process and why – which you might have documented within your data processing activities. Yet maintaining data protection requires a risk-based approach to data handling.
Let's illustrate with an example. Consider data security differences based on storage methods. Storing employee data on an open network poses higher risk levels. Implementing security measures like access control dramatically lowers this risk.
By identifying and acting on these risk types, you minimise chances of experiencing issues like data breaches.
We conduct GDPR risk assessments to stay ahead of problems. This helps spot risks and weaknesses before they lead to personal data mishandling.
GDPR Risk Assessment Best Practices
Conducting effective GDPR risk assessments is crucial for protecting personal data and meeting legal requirements. While detailed guidance exists from Data Protection Authorities, we offer a practical step-by-step guide to simplify the process.
Step-by-Step GDPR Risk Assessment Process
1. Identify Data Processing Areas
Start by finding where personal data is processed in your organisation. Determine specific information types you handle. Remember, documenting this is already a GDPR requirement as part of your official data processing activities and records.
2. Understand Threats to Data Subjects
Think about and identify threats from your data processing work. Use your chosen framework to outline possible threat scenarios. Ensure these scenarios remain relevant to your organisation.
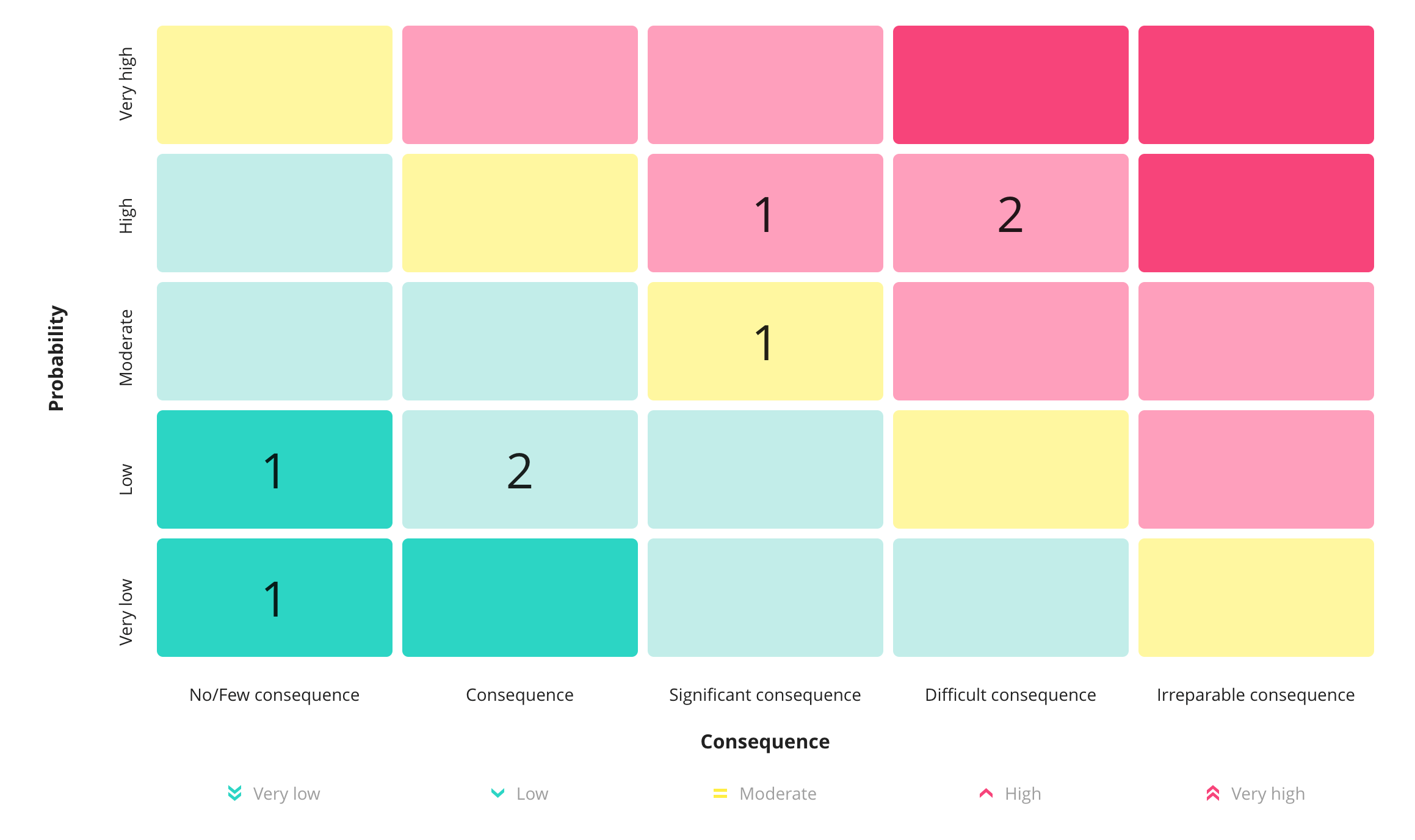
3. Calculate Risk Levels
Look at each identified threat. Assess how much risk it poses to your data processing. Consider two things: likelihood of occurrence and potential impact on the person whose data it is. Using these elements, create a risk matrix. This helps determine a risk score, recommended by Data Protection Authorities.
4. Highlight High-Risk Areas
After assessing all data processing tasks, focus on high-risk areas. Know your organisation's general "risk tolerance" level. Pay special attention to activities with high or very high risk levels.
5. Implement Risk Mitigation Measures
In high-risk areas, implement specific security steps. Either lessen the possible impact of a threat or reduce its likelihood. Keep updating your GDPR risk assessment to ensure measures actually make a difference.
Justifying Your GDPR Risk Assessment Choices
When exploring data processing activity details, performing GDPR risk assessments becomes crucial. It's important to articulate your reasoning for each assessment clearly and precisely. This serves several purposes:
Self-Understanding: Clear justifications ensure consistent decision-making approaches and allow later reflection on choices.
External Communication: Sometimes external parties – DPOs, regulators, or stakeholders – may ask for GDPR risk assessment details. Clear argumentation helps them understand your process.
The consequence assessment examines possible outcomes of specific data activities and particular threats. These outcomes vary widely – from severe issues like identity theft to complex situations like harassment. Thorough understanding of possible outcomes makes risk scores more nuanced and accurate.
The probability assessment should base on current security measures you've implemented. These might include technical solutions like firewalls or organisational steps like physical access control or pseudonymisation. Taking time to consider how these measures lower risk helps justify probability scores accurately.
Each threat scenario needs tailored justification, just like risk scores. This highlights the need to dedicate sufficient time and attention to each GDPR risk assessment step, allowing careful justification of actions.
GDPR Risk Assessment Framework
Risk assessment can seem complex, but well-developed frameworks simplify the process and improve assessment accuracy. This framework should serve as a systematic guide through many risk assessment aspects.
Let's examine different steps a framework includes:
1. Start with Clear Overview Every GDPR risk assessment should begin by mapping activities involving personal data. Consider which systems, data processors, and third parties have data access.
2. Create Risk Scenarios Create scenarios to visualise potential threats. Although scenarios vary in complexity, they should closely tie to relevant data activities.
3. Use Relevant Information Add detailed information to each scenario. This information should come from specific data activities, allowing deeper understanding of real risks.
4. Document Security Measures Familiarise yourself with existing security measures protecting personal data. This covers both technical solutions and organisational measures.
5. Develop Consequence Catalogue A systematic overview of potential data breach consequences helps with proactive planning. With a predefined catalogue, you easily identify likely and severe outcomes.
6. Assess Each Activity With all components in place, carry out the actual GDPR risk assessment. Review each scenario for every processing activity and assign risk scores.
An effective framework provides an approach to assessing personal data risks. This gives organisations the best foundation for making well-informed data protection decisions. Individual employees also benefit from this strong foundation.
GDPR Risk Assessment Example
Based on the above framework, we'll create a simplified GDPR risk assessment example. This focuses on a data processing activity called "Payroll" – processing employee information connected to salary payments.
Scenario 1: Unauthorised Access Risk
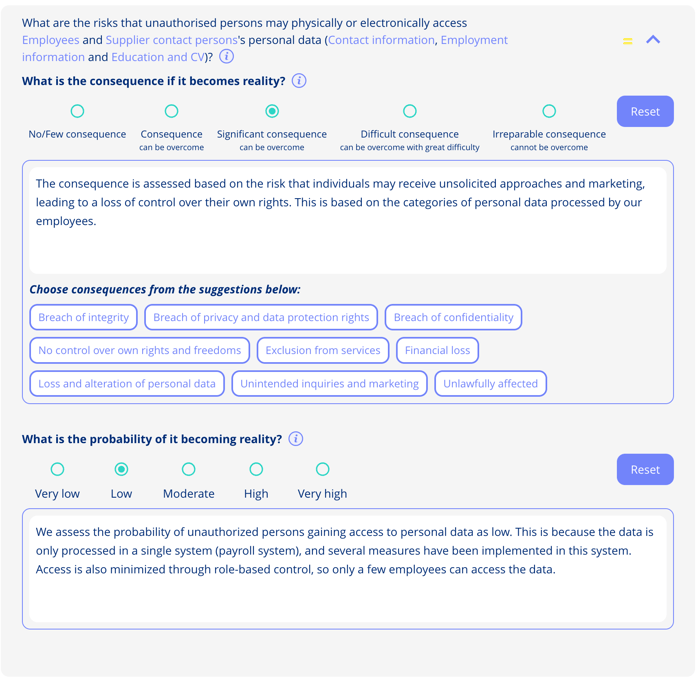
"What's the risk of unauthorised persons gaining physical or electronic access to employee personal information (Contact information, Employee information, Financial information, Social Security Number)?"
Consequence Assessment: 3 (Significant consequences, can be overcome)
Reasoning: The consequence is assessed based on risk that individuals may receive unsolicited approaches and marketing, leading to loss of control over their rights. This bases on the categories of personal data processed for employees.
Probability Assessment: 2 (Low)
Reasoning: We assess probability of unauthorised persons gaining access to personal data as low. Data is only processed in a single system (payroll system), with several implemented measures. Access is minimised through role-based control, so only few employees can access data.
Risk Level: Moderate
Scenario 2: Legacy System Storage Risk
"What's the risk of personal information (Contact information, Employee information, Financial information, Social Security Number) being stored in phased-out IT systems?"
Consequence Assessment: 2 (Consequences, can be overcome)
Reasoning: If this occurred, there would be prolonged periods during which personal data could be hacked and exposed to cyber attacks.
Probability Assessment: 1 (Very Low)
Reasoning: We only perform payroll processing in a single central system that's active and updated regularly according to our IT security policy. When our previous payroll system was phased out 5 years ago, data was first pseudonymised and later deleted as documented and validated.
Risk Level: Very Low
Overall GDPR Risk Assessment for "Payroll" activity: Moderate
Conclusion
Navigating GDPR can feel overwhelming, but robust frameworks transform complex landscapes into structured, manageable processes. Our "Payroll" example uses carefully crafted risk scenarios and methodical records, making the GDPR risk assessment process transparent.
Structured frameworks offer many benefits:
Avoiding Analysis Paralysis: This approach allows well-considered decisions without feeling overwhelmed by details.
Integrating Data Protection: It's not solely about meeting legal requirements – the goal is fostering a culture where data protection is central to all work processes.
Depending on your organisation's needs, tool choices vary. You might opt for simpler tools like Word or Excel, or choose specialised GDPR compliance platforms.
At .legal, we offer comprehensive compliance solutions. Our platform provides users with predefined risk scenarios, comprehensive catalogues, and easy integration of data and processes. This ensures holistic approaches to GDPR risk management.
The images used in this article are from the Privacy platform's risk module.
GDPR Compliance Software




.jpeg)

.jpg)
.jpg)



.jpg)

-1.png)



.jpeg)








.jpg)





Info
.legal A/S
hello@dotlegal.com
+45 7027 0127
VAT-no: DK40888888
Support
support@dotlegal.com
+45 7027 0127
Need help?
Let me help you get started

+45 7027 0127 and I'll get you started
.legal is not a law firm and is therefore not under the supervision of the Bar Council.